One email. One click. And just like that, your company’s data, customer records, or financial accounts could be in someone else’s hands.
Phishing attacks are that quick and devastating. No matter how smart or cautious your team is, it only takes one well-crafted message to fool even your most security-savvy employee.
Modern phishing emails don’t always have obvious red flags. They can look like a routine Microsoft login request, an internal file share, or even a simple invoice. Easy to trust and dangerously easy to fall for.
The good news is that there are fast, effective ways to catch these attacks before any damage is done. Let’s discover how.
Signs of a Phishing Attack
While phishing emails are getting harder to catch, there are still some signs that can raise a red flag.
Here are a few quick checks that can save your company from serious trouble:
- Strange sender addresses: Even if the name looks familiar, hover over the sender’s email address. A slight misspelling or a random domain name is often a giveaway.
- Urgent requests: “Act now!” “Your account will be locked!” Urgency is a classic phishing trick to get you to click without thinking.
- Unfamiliar links: Always hover over links before clicking. If the URL looks strange or doesn’t match the sender’s organization, it’s a major warning sign.
- Unexpected attachments: Be cautious with files you weren’t expecting, especially if the email feels slightly off or is pushing you to open something quickly.
Of course, attackers are getting smarter, and sometimes a phishing email can pass all these quick checks.
The Easiest Way to Spot a Phishing Attack (Without Taking Risks)
Many companies have come to a simple conclusion:
If employees can safely check suspicious emails before interacting with them, the chances of falling for phishing attacks drop dramatically.
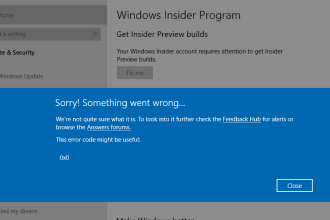
This is why they started using tools such as interactive sandboxes to safely investigate suspicious links and attachments without risking their networks.
Interface of an interactive sandbox called ANY.RUN with detected phishing attack
Instead of guessing whether a link or attachment is safe, employees can easily run it inside a controlled sandbox environment.
Here’s what happens:
- The suspicious link or file is opened inside the sandbox, not on the employee’s real machine.
- If the sandbox detects something malicious, like a fake login page or a hidden malware dropper, it immediately flags it.
- Employees can then report the threat to the security team without ever putting the company at risk.
| Give your team the easiest way to spot phishing attacks before they become costly mistakes.Sign up for ANY.RUN with your business email |
Real-World Example: Catching a Phishing Attack in Seconds
To see just how fast and easy it can be to detect a phishing attack, let’s take a look at a real phishing email analyzed inside one of the most user-friendly sandboxes out there: ANY.RUN.
View the full analysis session here
Phishing message displayed inside ANY.RUN sandbox
In this case, the phishing email pretends to be a system notification from Microsoft Office 365. At first glance, it looks somewhat believable: a “system message” alerting the user about undelivered emails and prompting them to click on “View Returned Messages.”
Inside the sandbox, we can safely open and interact with this message without risking any real damage.
The moment the user clicks the “View Returned Messages” button, they are redirected to a fake Microsoft login page, designed to steal their credentials.
Fake Microsoft login page opened inside the interactive sandbox
A closer look at the URL reveals something suspicious right away: The link has nothing to do with Microsoft’s official domain. Instead, it’s a strange address packed with random characters and unfamiliar names; a classic red flag.
If a victim were to enter their login information here, the attackers would immediately capture their credentials, gaining unauthorized access to corporate emails, sensitive documents, or even cloud services.
But thanks to ANY.RUN’s dynamic analysis, you don’t even need to guess.
On the right side of the screen, the sandbox automatically detects and labels this behavior as “phishing”, giving a clear warning to users and security teams before any real harm can happen.
Malicious activity detected by ANY.RUN sandbox
Protect Your Company by Detecting Phishing Attempts Early
Stopping phishing attacks doesn’t have to be complicated or slow.
With the right tools, your employees can investigate suspicious emails safely, without putting your business at risk and without needing any advanced technical skills.
Using an interactive sandbox like ANY.RUN, your team can:
- Detect phishing emails in under 40 seconds
- Analyze suspicious links and attachments without leaving the browser
- Flag threats before they reach sensitive data
- Empower employees to report phishing without fear of making a mistake
Sign up with your business email and start to proactively analyze threats today.